Enthusiasts of personal audio devices will likely be familiar with the Fast Pair tech by Google. Unfortunately, it has been discovered that the tech has a flaw that allows hackers to hijack the feature. With that done, they can then not only listen in on you via said devices’ mic, they can also push audio through devices’ speakers.
What Is Google Fast Pair?
For the unfamiliar, Google Fast Pair is the tech that shortens the pairing process between compatible devices. Traditionally, you need to have, say, your phone, to have its Bluetooth turned on and discoverable, and the compatible audio device in pairing mode. This tech instead makes it so that only the latter is required, as the device checks for unpaired but compatible devices. If your phone or tablet is among them, you’ll see a popup reflecting that. Tap on that, and voila, your devices are now paired.
![]()
There are other benefits to Fast Pair beyond skipping the menu navigation. Because this is Google tech, your paired device is synced to your account. In the event that you need to change to another phone, your audio device will recognise that it’s yours. As long as you sign in to said account, anyway. This tech is also what lets your phone show the battery levels of connected devices. And finally, the tech is part of the Find Hub network, the tech used to find your devices.
So What’s The Deal With This Flaw?
Researchers at the Belgian KU Leuven University Computer Security and Industrial Cryptography group were likely the first to have discovered the vulnerability, dubbing it WhisperPair. What it does is forcefully pair a vulnerable audio product with a hacker’s device without the owner’s consent, naturally. Because it’s a flaw with the implementation of the Fast Pair tech, this gives the hackers the same amount of range as the tech itself to hijack your device. Which, as the researchers tested, can go up to 14m. And all it takes is 10 seconds.
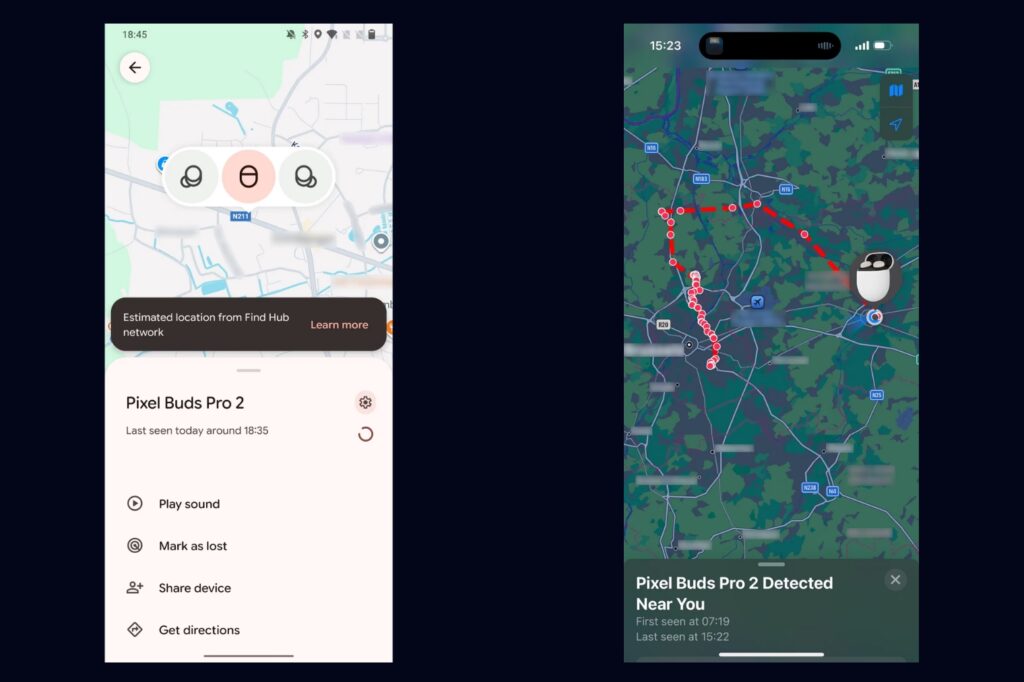
Once hijacked, the hackers can use your audio device in a couple of ways. Most obviously, it can take over the device’s mic to record audio. It can also be used to make the device play audio at high volumes. And with access to the Find My Device part of the tech, it can also be used to track your location and movement. This will still show up on your phone as someone tracking you, but because it shows your device, you may make the mistake of dismissing the notification. And this is what allows the hacker to stalk you for extended periods of time.
The Problem Is Not The Tech, But Poor Implementation Of It
Funnily enough, the existence of the flaw is less due to it being poorly made to begin with. Instead, the researchers attributed it to poor implementation. Or to cite the report, it exists because “many flagship products have not implemented Fast Pair correctly”. But on the flip side, it’s not an “individual developer error” either. Rather, it’s indicative of a systemic failure, as affected devices passed both the manufacturer’s quality assurance tests and Google’s certification process.
For context, proper implementation of the tech would mean that, a phone sends a message via Bluetooth LE to the accessory. But when the accessory is not in pairing mode, it should ignore such messages. It’s when devices fail to do so that hackers’ devices can force the pairing process, establishing a Bluetooth connection after.
What Can I Do To To Stay Safe?
To prevent being a victim, you’ll unfortunately just have to exercise vigilance as usual. This is especially in the case of a device being hijacked to stalk victims as mentioned above. The good news is that the researchers reported their findings back in August of last year, agreeing to a 150-day disclosure window. In the five months since, Google has worked with hardware partners in developing and rolling out a fix.
On one hand, you will likely be safe just by installing software updates as they get released. But on the other, there’s no guarantee that your specific device has already gotten its security patch. There’s a handy list, linked below, of what devices are still vulnerable, and there’s a surprising number of Sony devices there, at least at the time of writing.
(Source: KU Leuven COSIC [1], [2])

