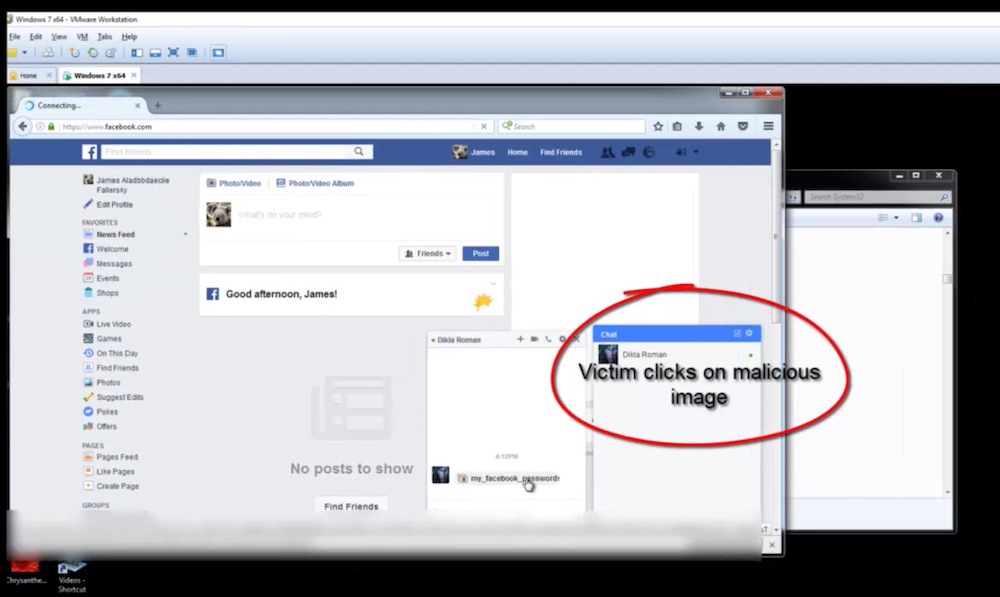
Researchers recently discovered that attackers are using a new way to distribute malware through images. Called ImageGate, the attackers will embed malware in images on popular social media applications such as Facebook and LinkedIn, and once a user opens the file, their device will be infected.
According to Check Point researchers, the attackers uploads malicious code by exploiting a flaw in the way these website handle images. It will deliberately force victims to download the image file, and once opened, their system will be hijacked and files are encrypted until you pay up.
https://www.youtube.com/watch?v=sGlrLFo43pY
While it is relatively easy to avoid being attacked simply by not opening unknown files, what makes the Locky ransomware scary is that it targets major websites that are usually trusted by everyone – no one would expect something downloaded from Facebook would be malicious.
Fortunately, Facebook is already aware of the problem. A spokesperson from the social media says that it isn’t a case of ransomware, instead, it’s simply really “bad Chrome extensions” that sends messages to others, and they have already blocked it several days ago.
Still, it’s better to be safe than sorry. According to Check Point, if you have clicked on an image and your browser starts downloading a file, do not open it, and do not open any image file with unusual extensions like SVG, JS or HTA.
(Source: Check Point via: Engadget)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.