Amnesty International recently published a report called the “Intellexa Leaks”, a joint investigation by Inside Story, Haaretz, and WAV Research Collective. The report details the operations of Intellexa, a surveillance company, and its product, a spyware called Predator.
While not a household name, Intellexa is widely known among hackers and cybersecurity groups as one of the most notorious mercenary spyware companies. At its core, the business essentially develops spyware and sells it to governments. The Intellexa Leaks provide insight into the company’s inner workings, and more specifically, details about its zero-click spyware, Predator.
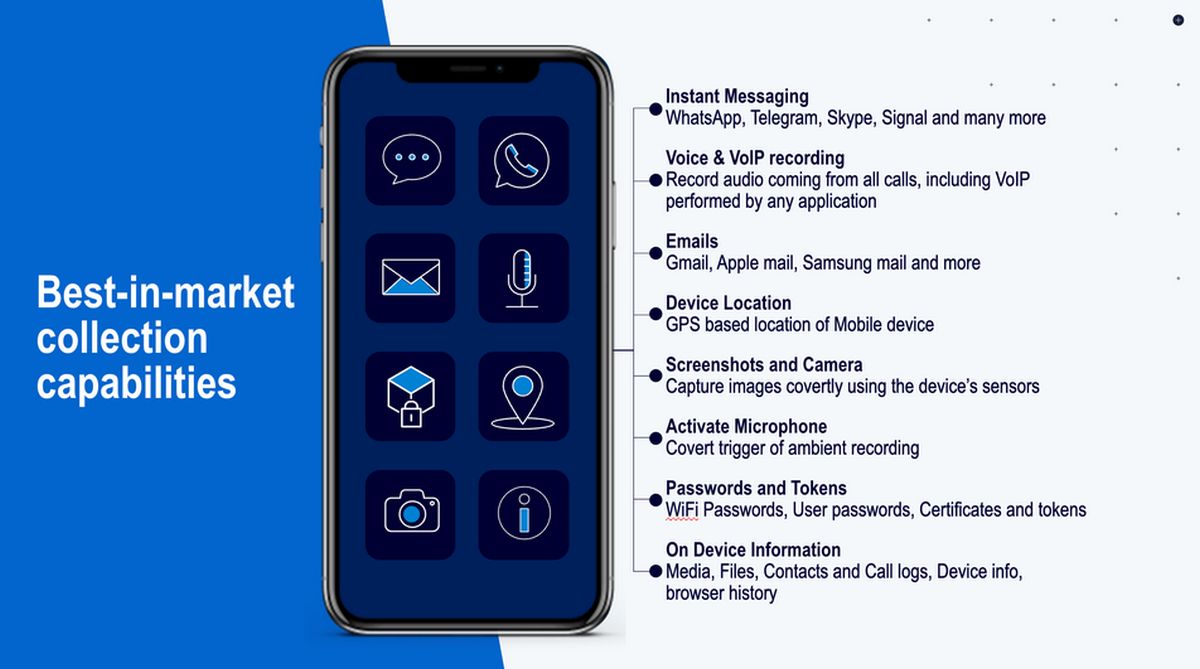
As per the description, Predator is designed primarily to infiltrate mobile devices; in its current state, the spyware is deployed in the form of a “targeted ad” on the victim’s phone, usually when accessing a site via their browser. Again, they don’t necessarily need to click or tap on anything. Once the “ad” is played, that’s it: their device is infected. From this point, the spyware can collect data from virtually any app, be it from WhatsApp, keylogging, emails, or pictures taken with the phone’s camera.
Where Predator Is Active
Pakistan has been fingered as the country where the Predator spyware is currently active. This year, one of its victims, a human rights lawyer from the country’s Balochistan’s province, received a malicious link over WhatsApp from an unknown number. Long story short, they clicked on the link, and their phone was infected with Intellexa’s product. The Pakistani government has denied any claims that such spyware was being widely used within its borders.
The Many Faces Of A Predator
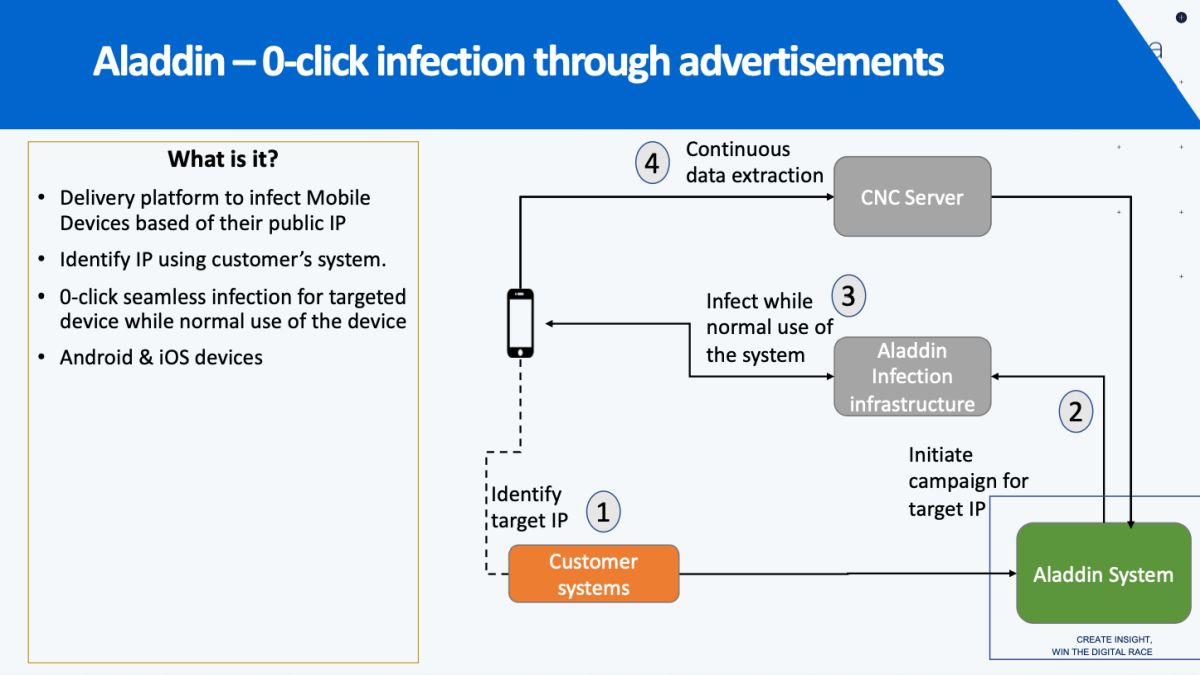
Predator isn’t the only name the spyware goes by. The Intellexa Leaks show that it has been renamed and remarketed as Helios, Green Arrow, and Red Arrow. As of now, its parent company has developed a new form of it, codenamed Aladdin, as a new strategic infection vector, which uses the zero-click attack that we’ve talked about.
“While technically complex to implement, the attack itself is conceptually simple. The Aladdin system infects the target’s phone by forcing a malicious advertisement created by the attacker to be shown on the target’s phone. This malicious ad could be served on any website which displays ads, such as a trusted news website or mobile app, and would appear like any other ad that the target is likely to see. Internal company materials explain that simply viewing the advertisement is enough to trigger the infection on the target’s device, without any need to click on the advertisement itself.”
This is just a layman’s summary of Amnesty’s entire report, and if you want the full breakdown of the Intellexa Leaks on Predator, we strongly recommend that you read it at the source.
(Source: Amnesty International)


