It’s been a while since Intel last had a major issue in its CPUs, with the Spectre and Meltdown vulnerabilities being the most prominent flaws in 2018. Recently, a bunch of university academics discovered two new vulnerabilities that seemingly affect Intel CPUs, but are mercifully, not quite as daunting as the other two flaws.
To be precise, the researchers simply referred to the vulnerabilities as “different attack methods”, known officially on paper as SGAxe and CrossTalk. The flaw also affects Intel CPUs launched between 2015 and 2019. As per their report, SGAxe looks and functions similarly to the CacheOut attack that also came to light last year. Where hackers would exploit the processor’s L1 cache to gain access and extract information.

In this case, SGAxe was described as the fruit of Intel’s failure to mitigate side-channel attacks against Software Guard Extensions (SGX); by executing what is called a “transient execution attack”, an attacker is technically able to recover the cryptographic keys stored within the SGX. Thus enabling them to access security-sensitive files, such as financial transactions or DRM-protected content.
The second flaw, CrossTalk, is supposedly a variant of Microarchitectural Data Sampling (MDS). To put it plainly, for this exploit, hackers can gain access to the affected CPU and its system by simply injecting a specially crafted piece of software that runs on one CPU core. And then compromise the private keys to a piece of software running on a separate core.
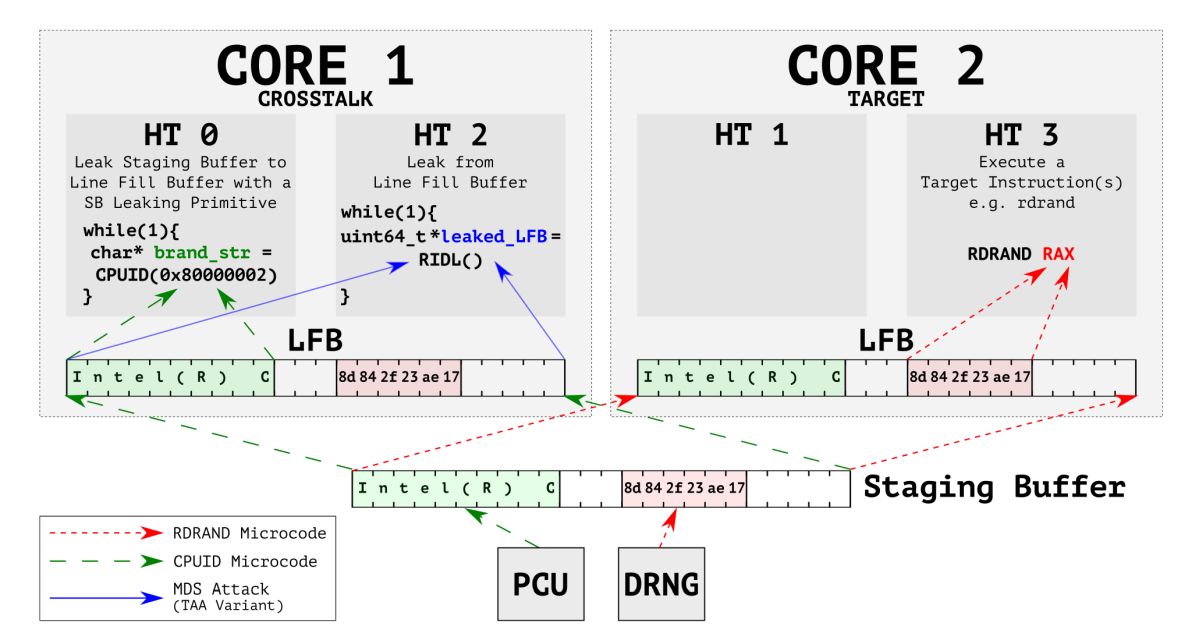 The good news is that, unlike Spectre and Meltdown, Intel says that the chances of people actually executing these attacks outside of a controlled environment is highly unlikely. Of course, in keeping with the “better safe than sorry” spirit, Intel said that it will be releasing a microcode update to the vulnerabilities as soon as it possibly can.
The good news is that, unlike Spectre and Meltdown, Intel says that the chances of people actually executing these attacks outside of a controlled environment is highly unlikely. Of course, in keeping with the “better safe than sorry” spirit, Intel said that it will be releasing a microcode update to the vulnerabilities as soon as it possibly can.
(Source: Techspot)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.


