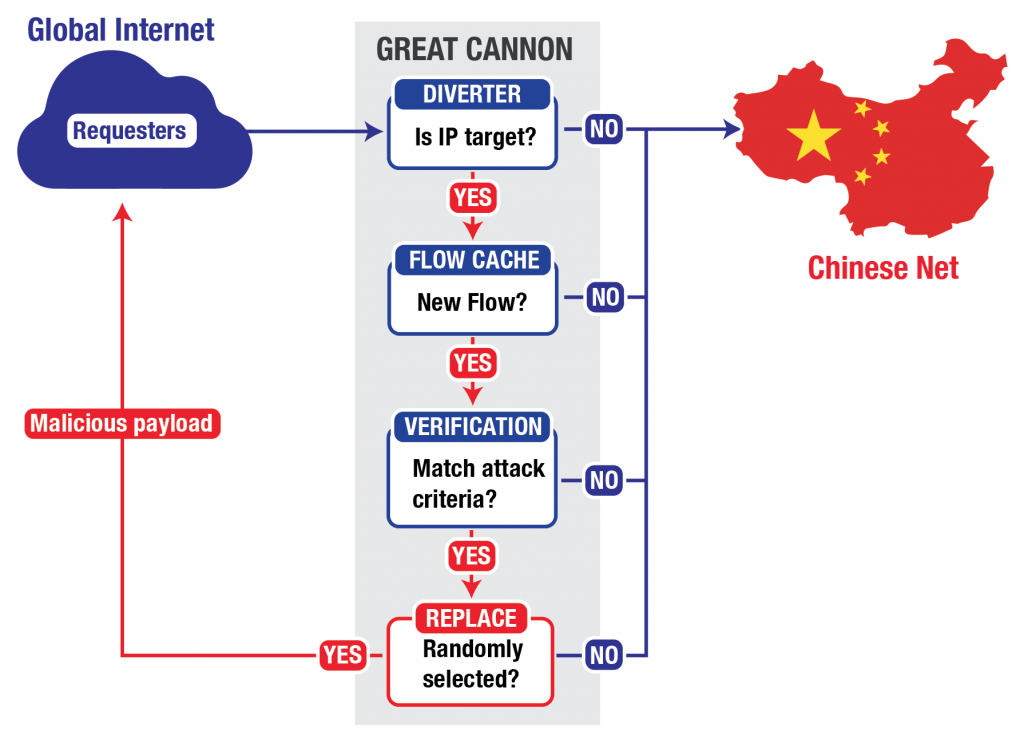
Several anti-censorship site came under DDoS attack last month, an act that investigators noted came out of China. While many suspected that the Great Firewall of China was being turned into a weapon, the truth has turned out to be much worse. Calling it the “Great Cannon”, researchers have uncovered details about China’s latest internet weapon.
Both GreatFire.org and a mirror site for the Chinese version of the New York Times came under heavy DDoS attack last month, and what was unusual was sustained length of the attack. It lasted for close to a week, and did not abate despite defensive measures being taken.
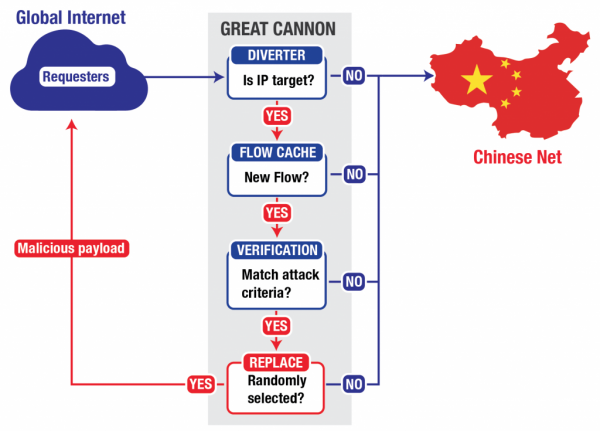
Researchers at the time noted that the attack was coming out of China, which had apparently repurposed ads to redirect traffic at the targeted websites. However, new information indicates that this was only a small part of the Great Cannon, which intercepts foreign traffic coming into the country. This not only allows its to monitor all incoming traffic, but also alter it as the government sees fit. It could be that the DDoS attack last month was simply a trial run, and the Chinese government is still fine tuning how the weapon works.
Internet users do not even have to surf into Chinese websites like Baidu, where the original attack came from, to become trapped by the Great Cannon. Researchers speculate that any site serving ads from China could also potentially end up injecting malicious code into computers.
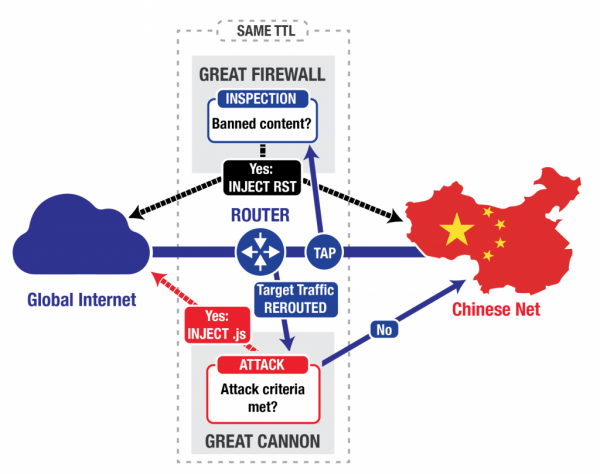
While the DDoS attack was a demonstration of what the Great Cannon is capable of, it doesn’t appear to be the only thing it can do. The system is built into China’s internet backbone, which allows it access to all traffic. Unlike the Great Firewall that is an “on-path” system that is designed mainly for eavesdropping on communications. Although both function as very powerful tools for online censorship.
That being said, China is not the first country to deploy this sort of cyber-weapon. Documents by Whistleblower Edward Snowden revealed a similar threat deployed by the American NSA and their British counterparts in the GCHQ. Called Quantum, the system functions in the same way as the Great Cannon; although neither the NSA nor the GCHQ has deployed it in such a blatant show of force.

Quantum was mainly used to redirect traffic to a site of the operators’ choosing in order to perform targeted surveillance. Not that the act was any less dangerous for the average internet user.
There is little that can be done when the source of the online threat happens to lie on the internet backbone of a country, and it will be interesting to see how nations respond to this latest turn of events.
[Source: The New York Times]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.